PYLE PLCMDVR49 - HD 1080p DVR Rearview Mirror Dash Cam Kit - Dual Camera Vehicle Video Recording System with Waterproof Backup Cam, 4.3'' -inch Display - Walmar… | Dashcam, Rear view mirror, Mirror kit

The Big Tesla Hack: A hacker gained control over the entire fleet, but fortunately he's a good guy | Electrek

Driving surveillance: What does your car know about you? We hacked a 2017 Chevy to find out. - The Washington Post



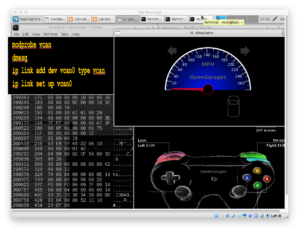
![CAN Bus Sniffer - Reverse Engineer Vehicle Data [SavvyCAN/Wireshark] – CSS Electronics CAN Bus Sniffer - Reverse Engineer Vehicle Data [SavvyCAN/Wireshark] – CSS Electronics](https://cdn.shopify.com/s/files/1/0579/8032/1980/files/CAN-bus-sniffer-reverse-engineering-car-hack.svg)











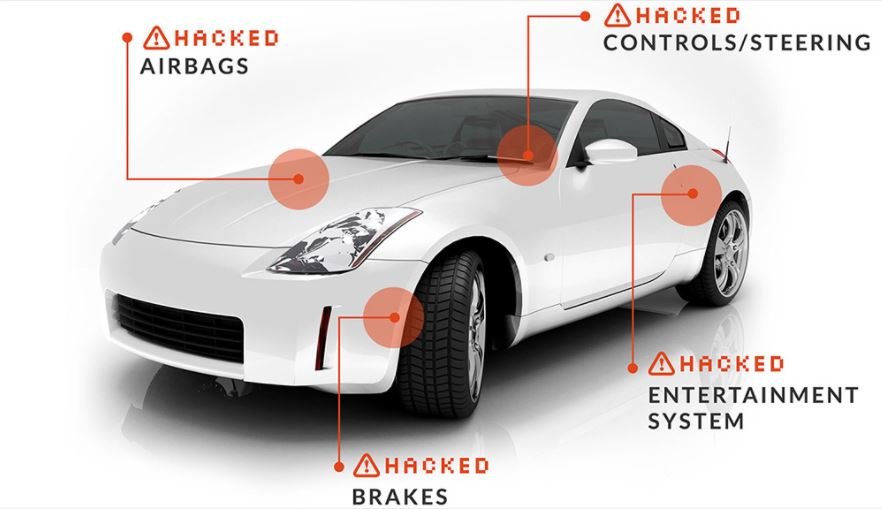
![CAN Bus Sniffer - Reverse Engineer Vehicle Data [SavvyCAN/Wireshark] – CSS Electronics CAN Bus Sniffer - Reverse Engineer Vehicle Data [SavvyCAN/Wireshark] – CSS Electronics](https://canlogger1000.csselectronics.com/img/control-your-car-hacking-vehicle-CAN-bus.svg)
:max_bytes(150000):strip_icc()/GettyImages-956353340-5762c67796d34710b08ad476a5e693d6.jpg)